X-Content-Type-Options HTTP Header
If you are a website owner or developer, you have probably heard about this header before, but you may not fully understand what it is or why it's important. In this article, we will cover everything you need to know about the X-Content-Type-Options HTTP header, including what it is, why it's important, and how to implement it on your website.
What is X-Content-Type-Options?
Web-based security risks are quite prevalent in today's technological age. Therefore, it is important to implement certain security measures to help avoid having your website compromised by an attacker. The X-Content-Type-Options is an HTTP header used to do just that - increase the security of your website.
The X-Content-Type-Options HTTP header is a security header that is designed to protect web applications from MIME type sniffing attacks. MIME type sniffing is a technique used by some web browsers to determine the MIME type of a file based on its content rather than relying on the MIME type that is declared in the Content-Type header. This can be a security risk because it can allow an attacker to execute malicious code on a website by tricking the browser into interpreting a file as a different MIME type than what it actually is.
The X-Content-Type-Options header was introduced to address this security issue. When the X-Content-Type-Options header is set to "nosniff", it instructs the browser to always use the MIME type that is declared in the Content-Type header rather than trying to determine the MIME type based on the file's content.
Why is the X-Content-Type-Options HTTP header important?
The X-Content-Type-Options HTTP header is important because it can help prevent MIME type sniffing attacks, which can be used to execute malicious code on a website. By setting the X-Content-Type-Options header to "nosniff", you can ensure that the browser always uses the correct MIME type, which can help prevent these types of attacks.
In addition to protecting your website from attacks, using the X-Content-Type-Options header can also help ensure that your website is displayed correctly in all browsers. Different browsers may handle MIME types differently, so by setting the X-Content-Type-Options header, you can ensure that your website is displayed consistently across all browsers.
How does X-Content-Type-Options work?
The X-Content-Type-Options header works by instructing the browser to always use the MIME type that is declared in the Content-Type header, rather than trying to determine the MIME type based on the file's content.
- A browser makes a request to a web server for an asset (e.g. image.jpg).
- A response is sent back with the header
X-Content-Type-Options: nosniff. This prevents the client from "sniffing" the asset to try and determine if the file type is something other than what is declared by the server. - The browser then accepts the MIME type defined by the origin server and displays the asset to the viewer.
What does it not protect against?
Unfortunately, the X-Content-Type-Options: nosniff header does not protect against all sniffing-related vulnerabilities. It is important to note that not all browsers support the X-Content-Type-Options header. However, all major modern browsers, including Chrome, Firefox, and Edge, do support it. This means that by using the X-Content-Type-Options header, you can protect your website from the majority of users who are using modern browsers.
But if an unsupported browser accessed an asset which sends back this particular response header, it won't have any effect.
Similarly, if a plugin or extension (e.g. Flash) is being used to fetch resources and also does not support this security header, there will be no protection in that scenario either.
Enabling the X-Content-Type-Options header
To enable this security header on your origin server is quite easily and can be done in just a couple steps. Depending upon which web server you're using will determine which snippet you should add to your server's configuration file. The following section outlines what needs to be added to both Nginx and Apache web servers.
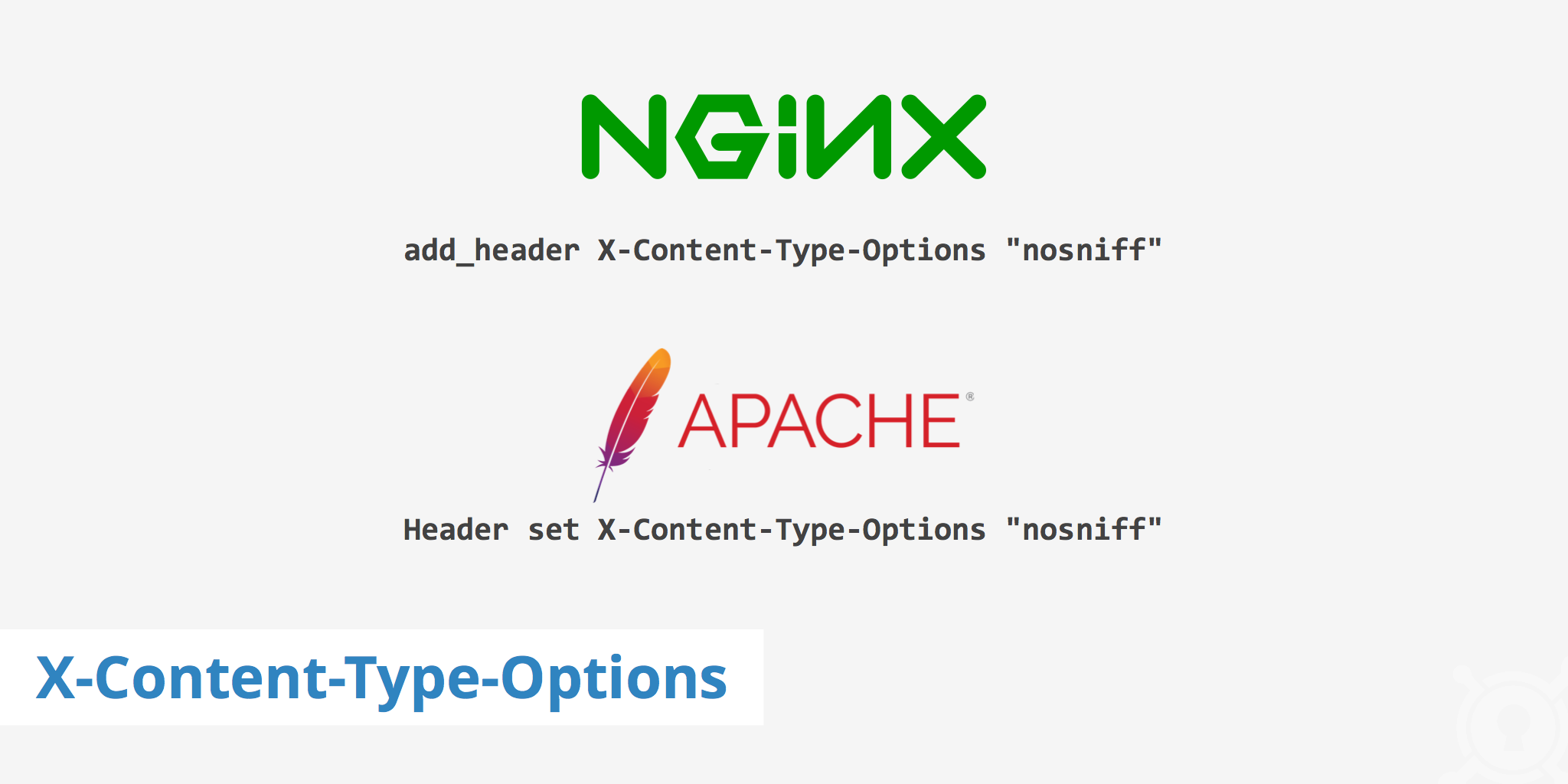
Nginx
For Nginx users, add the following snippet to your .conf file. Once done, save your changes and reload Nginx.
add_header X-Content-Type-Options "nosniff"
Apache
For Apache users, simply add the following snippet to your .htaccess file. Once done, save your changes.
Header set X-Content-Type-Options "nosniff"
Enabling your web server to deliver the X-Content-Type-Options header is quite simple to do. Although this web security header currently does not protect against all forms of XSS attacks, it is easy to implement and is certainly a step in the right direction towards a safer website.
Best practices for using the X-Content-Type-Options HTTP header
When using the X-Content-Type-Options HTTP header, there are a few best practices that you should follow to ensure that it is being used correctly.
First, it is important to ensure that the Content-Type header is set correctly for all files on your website. If the Content-Type header is not set correctly, the X-Content-Type-Options header may not work as intended. You can use a tool like the F12 Developer Tools in your browser to check the Content-Type header for each file on your website.
Second, it is recommended to use the X-Content-Type-Options header along with other security headers, such as the X-XSS-Protection and X-Frame-Options headers. These headers can provide additional protection against cross-site scripting (XSS) and clickjacking attacks.
Finally, it is important to test your website thoroughly after implementing the X-Content-Type-Options header to ensure that it is working as intended. You can use a tool like the SecurityHeaders scanner to check whether your website is using the X-Content-Type-Options header correctly.
Conclusion
In conclusion, the X-Content-Type-Options HTTP header is an important security header that can help protect your website from MIME type sniffing attacks. By setting the header to "nosniff", you can ensure that the browser always uses the MIME type that is declared in the Content-Type header, which can help prevent these types of attacks.
Implementing the X-Content-Type-Options header is relatively simple, and it is recommended to use it along with other security headers for maximum protection. By following best practices and testing your website thoroughly, you can ensure that the X-Content-Type-Options header is working as intended and providing the necessary security for your website.
Remember, website security should always be a top priority, and using security headers like the X-Content-Type-Options header can go a long way in protecting your website and your users.