What Is MIME Sniffing?
In today's digital age, the internet is an essential part of our lives. We rely on it for communication, entertainment, shopping, and much more. However, as we spend more time online, we expose ourselves to various security and privacy risks. One of these risks is MIME sniffing, a browser behavior that can compromise the security and privacy of our online activities.
Although MIME sniffing can be useful in determining an asset's correct file format, it can also cause a security vulnerability. This vulnerability can be quite dangerous both for site owners as well as site visitors. This is because an attacker can leverage MIME sniffing to send an XSS (Cross Site Scripting) attack. This article will explain how to protect your site against MIME sniffing vulnerabilities.
Understanding MIME Sniffing
MIME stands for Multipurpose Internet Mail Extensions, and it is a standard used to identify the type of content being sent over the internet, such as text, images, audio, video, and application files. MIME types are defined in the HTTP header of web requests and responses.
MIME sniffing, on the other hand, is a browser behavior that attempts to guess the MIME type of a resource if it is not explicitly specified in the HTTP header. The browser analyzes the content of the resource, looking for specific patterns or signatures that match known MIME types. If a match is found, the browser overrides the MIME type specified in the HTTP header with its own guess.
While MIME sniffing can be useful in some cases, it can also lead to security and privacy risks for users if exploited by attackers.
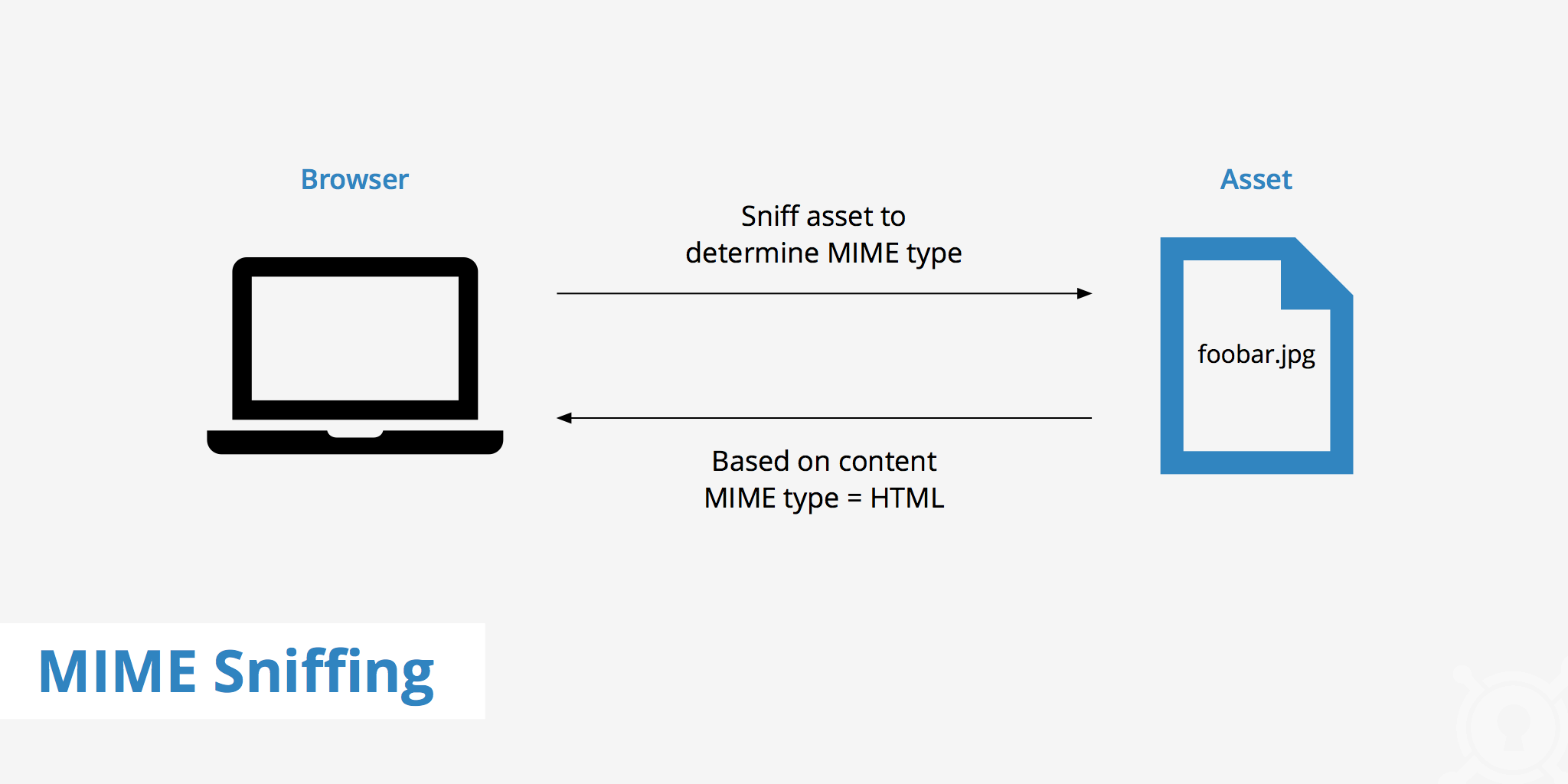
How does MIME sniffing work?
MIME sniffing is quite straightforward in the way that it works. The following provides a brief description of each step involved in the MIME sniffing process.
- A web browser requests a particular asset which responds with either no content type or a content type previously set at the origin server.
- The web browser "sniffs" the content to analyze what file format that particular asset is.
- Once the browser has completed its analysis, it compares what it found against what the web server provided in the
Content-Typeheader (if anything). If there is a mismatch, the browser uses the MIME type that it determined to be associated with the asset.
Why Does MIME Sniffing Matter?
MIME sniffing matters because it can lead to several security and privacy risks for users. Here are some examples:
Cross-site scripting (XSS) attacks
Attackers can use MIME sniffing to execute malicious code on a user's computer by tricking the browser into interpreting a file as a different MIME type than it actually is. This can lead to XSS attacks, where the attacker can steal sensitive information or perform actions on behalf of the user.
Content injection
Attackers can use MIME sniffing to inject malicious content into a web page, such as malware or phishing scams. The browser may not detect the content as malicious, and the user may unwittingly download or execute it.
Information leakage
MIME sniffing can reveal sensitive information about a user's browsing habits, such as the type of files they are downloading or viewing. This information can be used for targeted advertising or other purposes.
In the next chapter, we will explore how to protect ourselves from the risks of MIME sniffing.
How to avoid MIME sniffing vulnerabilities
MIME sniffing vulnerabilities can occur when a website allows users to upload data to the server. The vulnerability comes into play when an attacker disguises an HTML file as a different file type (e.g. a JPEG, zip file, etc.). Doing so would allow the attacker to successfully upload the file to the web server, assuming the web server accepts JPGs. Consequently, the browser will render it as an HTML file therefore providing the attacker with the possibility to execute XSS.
There are a couple of ways to avoid these kinds of attacks caused by MIME sniffing.
1. Implement the use of the X-Content-Type-Options: nosniff HTTP header
When this header is included in the server's response to a web request, it instructs the browser to enforce the MIME type specified in the HTTP header, and not to perform any MIME sniffing. This prevents the browser from guessing the content type of a resource, and reduces the risk of MIME sniffing attacks.
By using the X-Content-Type-Options: nosniff header, web developers can ensure that the browser interprets the content of a resource as the specified MIME type, even if the MIME type is not explicitly set in the HTTP header. This helps to prevent attackers from exploiting MIME sniffing vulnerabilities to execute malicious code or inject malicious content into a web page.
It is important to note that not all browsers support the X-Content-Type-Options: nosniff header, and some older browsers may ignore it. However, most modern browsers do support it, and it is still a valuable security measure to implement.
2. Use content security policy (CSP)
Content security policy is a security mechanism that allows web developers to specify which resources can be loaded by a web page, and how they can be used. CSP can prevent MIME sniffing by enforcing strict rules for content types, and by blocking scripts or other resources that do not meet the specified criteria.
3. Use proper MIME types
Web developers should always specify the correct MIME type for each resource they serve, and ensure that it matches the content of the resource. This can prevent browsers from guessing the wrong MIME type, and reduce the risk of attacks or information leakage.
4. Disable MIME sniffing
Most modern browsers allow users to disable MIME sniffing, either through configuration settings or add-ons. Disabling MIME sniffing can prevent browsers from guessing the MIME type of a resource, and force them to rely solely on the HTTP header.
5. Keep your browser up-to-date
Browser updates often include security fixes and improvements that can mitigate the risks of MIME sniffing and other vulnerabilities. Make sure to regularly update your browser to the latest version, and enable automatic updates if possible
6. Using a separate subdomain
Using a separate subdomain to host and deliver all user uploaded content is another effective strategy for protecting against MIME sniffing. By hosting user-generated content on a separate subdomain, web developers can isolate it from the main domain and enforce stricter security policies, such as a different content security policy or a more limited set of allowed MIME types. This can reduce the risk of MIME sniffing attacks and minimize the impact of any potential vulnerabilities.
In addition, separating user-generated content from the main domain can make it easier to manage and update the security measures for that content specifically. For example, if a vulnerability is discovered that affects a specific MIME type, web developers can quickly apply a fix to the subdomain without affecting the rest of the website.
However, it is important to note that this strategy is not foolproof and may not completely eliminate the risk of MIME sniffing. Attackers may still attempt to exploit vulnerabilities in the subdomain, or use other techniques to trick the browser into executing malicious code.
Therefore, it is crucial to combine this strategy with other security measures, such as the ones mentioned above, to create a comprehensive and robust defense against MIME sniffing and other threats.
Conclusion
In conclusion, MIME sniffing is a browser behavior that attempts to guess the MIME type of a resource if it is not explicitly specified in the HTTP header. While it can be useful in some cases, it can also lead to security and privacy risks for users if exploited by attackers. MIME sniffing can be used for cross-site scripting attacks, content injection, and information leakage, among other things.
To protect yourself from MIME sniffing, you can use content security policy, specify proper MIME types, disable MIME sniffing, and keep your browser up-to-date. By following these steps, you can reduce the risk of falling victim to MIME sniffing attacks and keep your online activities secure and private.
As web browsing becomes more ubiquitous, it is important to be aware of the potential risks that come with it. By taking a proactive approach to online security, you can minimize your exposure to threats like MIME sniffing and stay safe while enjoying the benefits of the internet. So, keep these tips in mind and browse with confidence!