What Is a Botnet?
Today, we're going to talk about botnets. If you're not familiar with the term, don't worry - by the end of this article, you'll have a solid understanding of what a botnet is, how it works, and what you can do to protect yourself.
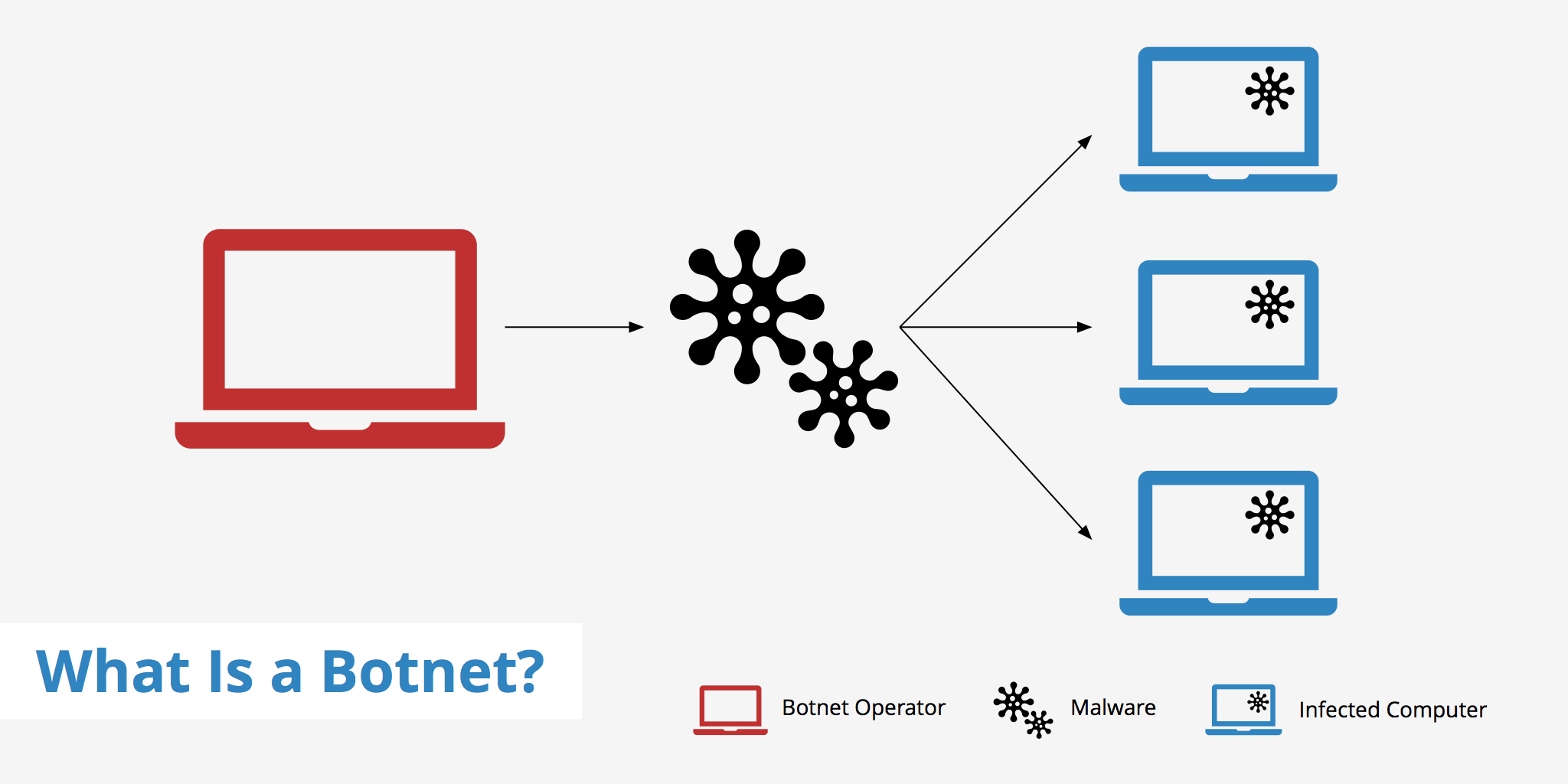
What is a botnet?
A botnet is comprised of multiple computers working together with the objective of completing repetitive tasks. Although in most cases, the term botnet is usually associated with the thought of a malicious attack, there exists both legal and illegal botnets. Legal botnets can be utilized for keeping internet relay chat channels free from unwanted users for example, while illegal botnets are widely seen used in DDoS attacks and other nefarious activities.
This article will focus primarily on illegal botnets as they are becoming increasingly apparent in today's technological ecosystem.
How do computers get infected?
Botnets are created by infecting multiple systems with malware (malicious software) and thus rendering them to be slave systems to the botnet operator. This malware can be introduced to a computer system in various forms, for example:
- A trojan within an email attachment: Malware can be attached to an email in the form of a file or link. When the user opens the attachment or clicks the link, the malware is downloaded and installed on their computer.
- Drive-by downloads: Malware can be downloaded and installed on a computer simply by visiting a compromised website. The user doesn't have to click on anything - the malware is automatically downloaded and installed in the background.
- Social engineering: Malware can be disguised as a legitimate program or update. The user is tricked into downloading and installing the malware, thinking that they are installing something useful.
Once the malware is installed, it can connect to the host computer who is now able send commands and control the slave machine remotely. Many users are unaware that this type of malicious software even exists on their computers since it does not affect the normal operations of the machine. However, unbeknownst to them, these trojans and other malware run unwanted commands in the background.
Example
A botnet can be created for a variety of purposes. In many cases, botnets today are created with the goal to be rented out to people wanting to send a targeted attack. The following example demonstrates the process of using a botnet for the purpose of sending out email spam.
- Multiple machines are infected with the malware sent out by the operator
- The slave machines log in to a command and control server where the botnet operator can issue commands
- A spammer rents the botnet from the operator
- The operator sends out the spammer's message to the command and control server resulting in the mass delivery of spam messages
Types of botnet attacks
Botnet attacks come in many forms. They can be used to do everything from overloading a web server with requests, to illegally generating revenue. The following is a list of a few popular types of botnet attacks.
- Distributed denial of service: DDoS Attacks are used for the purpose of making a website inoperable by overloading the server with requests.
- Click fraud: Botnets can be used to command a user's computer to click on PPC campaigns or other ads for personal monetary gain.
- Email spam: As described in the section above, email spammers can rent a botnet from the operator to send out a mass spam email campaign.
- Mining cryptocurrency: Bot herders can use the processing power of the infected computers to mine cryptocurrency. This can be a lucrative activity, as the bot herder doesn't have to pay for the electricity or hardware.
- Adware: Replaces the current ads on a web page with the ads of another advertiser for personal or commercial gain.
- Stealing sensitive information: Bot herders can use the infected computers to steal sensitive information, such as login credentials, credit card numbers, or personal information. This information can be used for identity theft or sold on the black market.
- Spreading malware: Bot herders can use the infected computers to distribute malware to other computers. This can be used to expand the botnet, or to carry out other malicious activities.
The list above are a few examples of how botnets can be used. One of the largest known botnets, called Zero Access Botnet, was in existence during 2013 and infected a combined total of 1.9 million machines. It used its army of slave computers for both Bitcoin mining and click fraud purposes to generate revenue.
How to protect against a botnet infection
Fortunately, there are a number of steps you can take to protect yourself from botnets. Here are some tips:
Keep your software up-to-date
Malware often takes advantage of vulnerabilities in software to infect computers. By keeping your software up-to-date, you can ensure that any known vulnerabilities are patched.
Use antivirus software
Antivirus software can detect and remove malware from your computer. Make sure to keep your antivirus software up-to-date, and run regular scans.
Be cautious with email attachments
Don't open email attachments from unknown sources or from sources you don't trust. Even if the email appears to be from someone you know, be wary of attachments that you weren't expecting.
Be cautious with links
Don't click on links from unknown sources or links that seem suspicious. Hover over the link to see where it leads before clicking on it and make sure the URL matches the site you were expecting to visit.
Use strong passwords
Use unique, strong passwords for all of your accounts, and enable two-factor authentication when possible. This can help prevent your accounts from being compromised.
Use a firewall
A firewall can help block unauthorized access to your computer or network. Make sure to enable the firewall on your computer or use a hardware firewall if you have a network.
Be cautious with public Wi-Fi
Public Wi-Fi can be a breeding ground for malware. Avoid logging into sensitive accounts, such as banking or email, on public Wi-Fi. If you must use public Wi-Fi, use a VPN to encrypt your traffic.
Be vigilant
Keep an eye out for suspicious activity on your computer, such as unexpected pop-ups or slow performance. If you suspect your computer may be infected with malware, run a virus scan and seek professional help if necessary.
Summary
n conclusion, a botnet is a network of infected computers used by cybercriminals to carry out various malicious activities. Botnets can be created through a variety of methods, such as email attachments, drive-by downloads, or social engineering. To protect yourself from botnets, it's important to keep your software up-to-date, use antivirus software, be cautious with email attachments and links, use strong passwords and two-factor authentication, use a firewall, be cautious with public Wi-Fi, and be vigilant for suspicious activity on your computer. By following these tips, you can help keep yourself safe from botnets and other malware threats.