Web Application Firewall
As businesses and organizations continue to rely on web applications for their day-to-day operations, the importance of securing these applications becomes increasingly critical. Cybersecurity threats such as SQL injection and cross-site scripting can exploit vulnerabilities in web applications and put sensitive data at risk. To combat these threats, many organizations are turning to a Web Application Firewall (WAF).
In this article, we will provide you with a comprehensive guide to WAF. You will learn what a WAF is, how it works, its benefits, and its types. So, without further ado, let's dive in.
What is WAF?
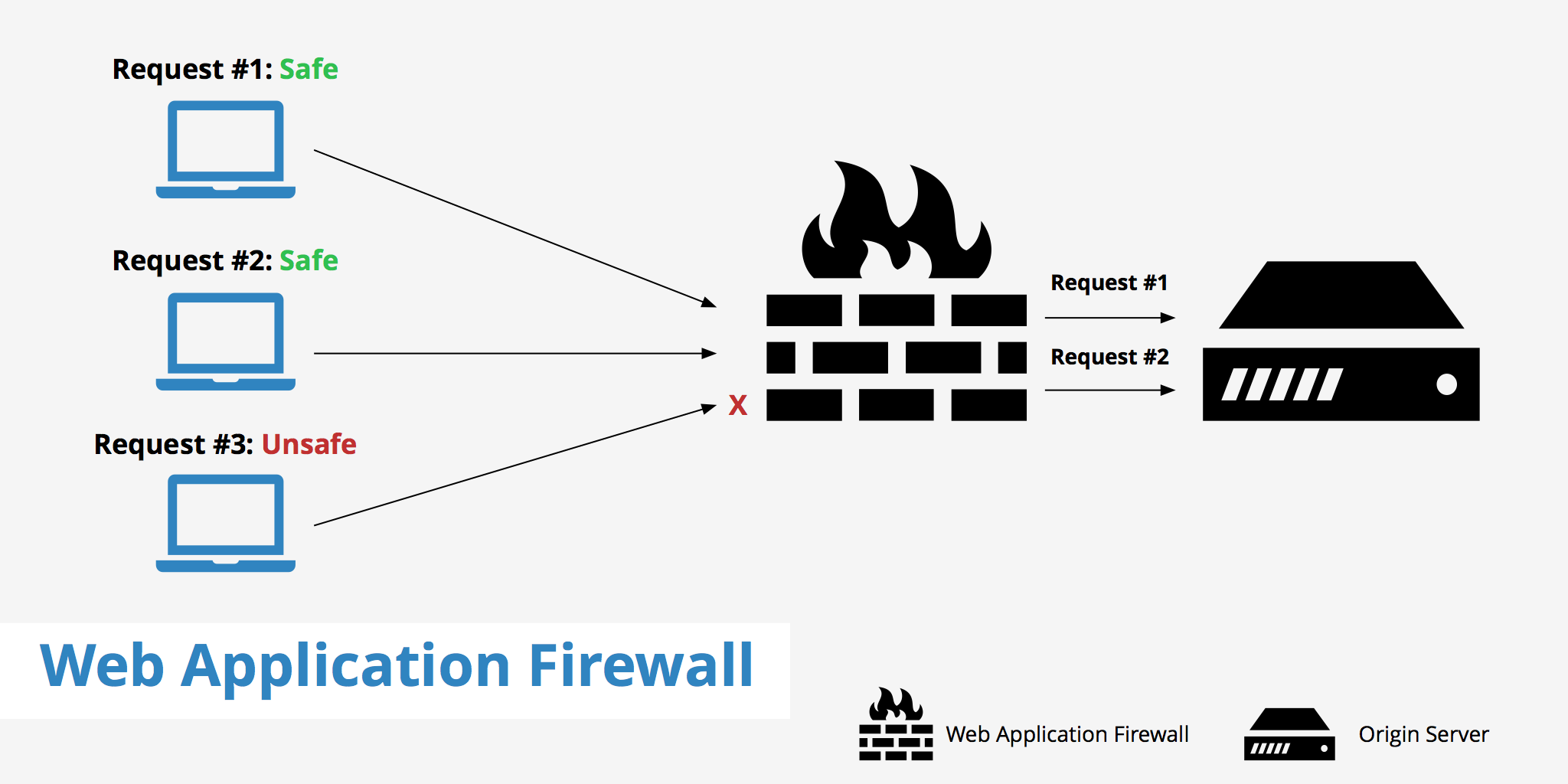
A web application firewall, or WAF, is a security measure that defines rule sets in order to help protect a web application from attack. The WAF monitors, filters, and blocks unwanted HTTP traffic that is going to and from the web application. Commonly, a WAF is used to protect against attacks such as cross-site scripting and SQL injection, however, can also be used to protect against illegal resource access, session highjacking, etc.
A WAF analyzes incoming traffic to web applications and applies a set of rules to determine if the traffic is legitimate or malicious. If the traffic is legitimate, it is allowed to pass through to the web application. However, if the traffic is deemed malicious, the WAF will block it, preventing it from reaching the web application.
How does it work?
A WAF will examine both the GET and POST requests to and from your origin server. Based on the rules that are configured, the firewall will distinguish between legitimate and illegitimate traffic. A web application firewall is also able to detect unusual behavioural patterns. For example if an attack causes the web application to send back much larger responses than expected, a WAF is able to detect that abnormality, and notify someone that there is an issue.
Another, more widespread, example of a WAF use may be it's ability to distinguish between spammy and legitimate comments on a blog by monitoring particular keywords. These comments will then be flagged as spam and discarded before reaching the comment section of your website.
As described by these examples, a WAF is simply an intermediary between the web application and the client. It can be thought of as a guard for your web application that helps to monitor and prevent traffic threats.
A WAF can operate in two modes: positive security model and negative security model.
Positive security model
The positive security model, also known as a whitelist, allows only known good traffic to pass through to the web application. The WAF blocks all other traffic that does not match the predefined criteria. This model is effective but requires a lot of maintenance to keep the whitelist up-to-date.
Negative security model
The negative security model, also known as a blacklist, allows all traffic to pass through to the web application, except for traffic that matches predefined criteria. The WAF blocks traffic that matches known attack patterns, such as SQL injection and cross-site scripting.
The negative security model is more flexible than the positive security model, as it can adapt to new attack patterns without the need for constant updates. However, it is also more prone to false positives, where legitimate traffic is blocked.
Benefits of a WAF
A WAF provides several benefits to organizations, including:
Protection against known and unknown threats
A WAF can protect web applications from known threats, such as SQL injection and cross-site scripting. Additionally, it can provide protection against unknown threats by identifying and blocking traffic that exhibits suspicious behavior.
Improved compliance
A WAF can help organizations comply with industry regulations, such as the Payment Card Industry Data Security Standard (PCI DSS). The PCI DSS requires organizations that handle credit card data to implement a WAF.
Reduced risk of data breaches
By blocking malicious traffic, a WAF reduces the risk of data breaches. This is important for organizations that store sensitive data, such as credit card numbers, social security numbers, and health records.
Improved performance
A WAF can improve the performance of web applications by caching frequently accessed resources and reducing the amount of traffic that reaches the web application. This can improve the user experience and reduce the load on the web application server.
How does WAF differ from IPS?
An IPS or, intrusion prevention system, is similar to a WAF in that it monitors network traffic for any abnormalities. It has the ability to log, alert and react in the event it finds a potential threat in the data from a packet. The main difference between WAF and IPS is a web application firewall is able to analyze layer 7 web application logic whereas IPS's cannot.
According to InfoSec aXioms, in order to distinguish a WAF from other security solutions, it should have the following capabilities:
- Deep understanding of HTTP: Having the ability to dissect the various parts of the HTTP protocol (parameters, headers, etc) is required for a WAF to effectively perform its tasks.
- Ability to whitelist: In the case that an attack cannot be detected using signatures, having the ability to whitelist allows the WAF to let traffic through that it knows to be valid.
- Session protection: A WAF should work hand-in-hand with the application's session management and protect from session-based attacks.
- Application layer rules: A WAF system should also be capable of a being signature based in order to apply application layer rules. These rules should be generic and able to detect variants of attacks.
- Allow exceptions: Exceptions should be able to be applied to parts of the application in order to avoid the possibility of false positives opening security gaps.
Distributed vs cloud-based web application firewall
There are two distinct forms of web application firewalls, distributed and cloud-based.
Distributed WAF
A distributed WAF is a type of WAF that is distributed across multiple servers, either physically or logically. The WAF is installed on multiple web servers, and each instance of the WAF monitors traffic for the web application on that server. The instances of the WAF communicate with each other to share information about incoming traffic and apply consistent security policies across all instances.
Distributed WAFs are typically used in large-scale environments where there are multiple web servers hosting a web application. They offer high availability and scalability, as they can be easily expanded by adding more instances of the WAF to additional web servers. They also offer improved performance, as each instance of the WAF is responsible for monitoring traffic for a subset of the web application.
Cloud-based WAF
A cloud-based WAF is a type of WAF that is hosted in the cloud, rather than on-premise. The WAF is provided as a service by a cloud provider, and the traffic for the web application is routed through the cloud provider's network. The WAF inspects the traffic and applies security policies, then forwards the traffic to the web application server.
Cloud-based WAFs are typically used by organizations that do not want to manage and maintain their own WAF infrastructure. They offer high availability and scalability, as they can be easily expanded by adding more resources to the cloud provider's network. They also offer improved performance, as the cloud provider's network is designed for high-speed, low-latency traffic.
Summary
In conclusion, a Web Application Firewall is an essential security tool for organizations that use web applications. It provides protection against known and unknown threats, improves compliance, reduces the risk of data breaches, and improves performance. There are two types of WAF: hardware-based and software-based. Choosing the right type of WAF depends on the organization's needs, budget, and technical expertise.
To ensure the best possible protection, it is recommended to use a WAF in conjunction with other security tools, such as a network firewall, antivirus software, and intrusion detection and prevention systems. By implementing a layered security approach, organizations can significantly reduce the risk of cyber attacks and protect sensitive data.
We hope this article has been informative and helpful in understanding the importance of a Web Application Firewall. Stay safe and secure!