SHA1 vs SHA256
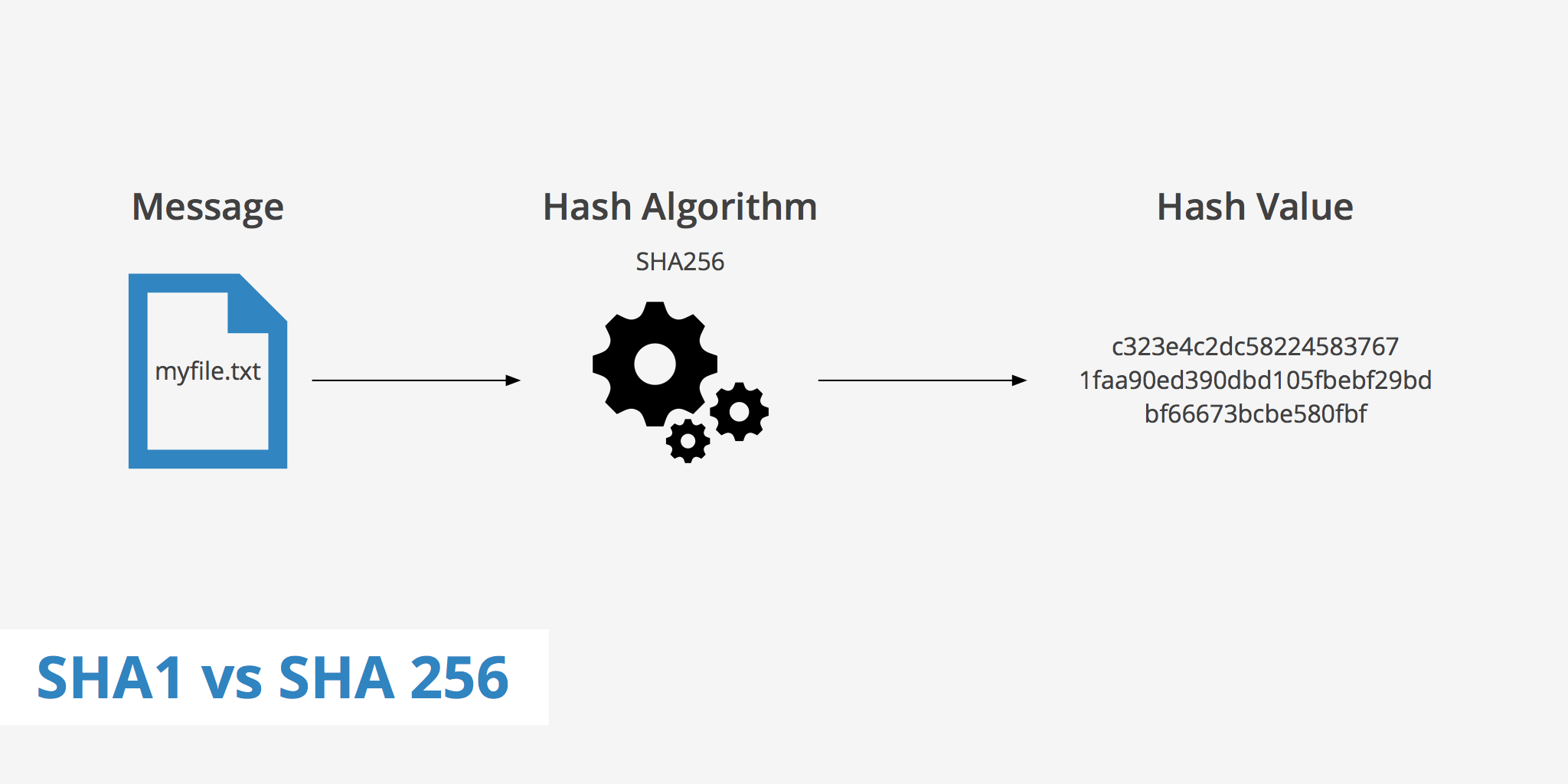
In today's world, security is of utmost importance, especially when it comes to data protection. We have all heard about data breaches and hacking incidents that compromise sensitive information. This is where cryptographic hash functions like SHA1 and SHA256 come into play. In this article, we will discuss SHA1 vs SHA256 and which one you should choose for your specific use case.
What is SHA?
SHA, which stands for Secure Hash Algorithm, is a cryptographic hashing algorithm used to determine the integrity of a particular piece of data.
SHA was developed by the National Security Agency (NSA) and published by the National Institute of Standards and Technology (NIST) in the United States. The SHA family of hash functions is widely used in digital signature protocols, message authentication codes, and other cryptographic applications that require data integrity and security.
This algorithm helps ensures that your website's data is not modified or tampered with. It does so by generating unique hash values from any particular file/variation of a file. Based on these hash values, it can be determined whether or not the file has been altered by comparing the expected hash value to the hash value received.
As computers become more powerful, the SHA hash sizes are increasing to help better improve security and make it harder for attackers to decrypt hashes. The secure hash algorithm originally started out as SHA0 (a 160-bit hash published in 1993).
As of when this article was published, there is currently a much more powerful SHA known as SHA3 (a 1600-bit hash). SHA-3 is a family of cryptographic hash functions designed by Guido Bertoni, Joan Daemen, Michaël Peeters, and Gilles Van Assche, and was selected as the winner of the NIST hash function competition in 2012. SHA-3 is a departure from the SHA-2 family in terms of its internal workings and structure. It uses a sponge construction that is based on a permutation, which enables it to be more resistant to certain types of attacks than the previous SHA algorithms. The output sizes of SHA-3 are the same as SHA-2, including SHA-224, SHA-256, SHA-384, and SHA-512.
The security of SHA-3 has been extensively studied, and it is currently considered to be a very strong and secure hash function. In fact, it has already been included in a number of widely-used cryptographic standards, including TLS 1.3 and IPsec.
However, it is worth noting that the strength of a cryptographic algorithm is not solely based on its design and implementation but also on its usage and configuration. To ensure the highest level of security, it is important to follow best practices for cryptographic usages, such as using appropriate key lengths, using strong and unique passwords, and keeping software and systems up-to-date with the latest security patches.
How do hashing algorithms fit into SSL/TLS?
Hashing algorithms play an important role in the SSL/TLS (Secure Sockets Layer/Transport Layer Security) protocol, which is used to provide secure communication over the Internet. SSL/TLS uses a combination of symmetric and asymmetric cryptography, along with hashing algorithms, to ensure the confidentiality, integrity, and authenticity of data transmitted between two endpoints.
When a client initiates a connection to a server over SSL/TLS, the two endpoints negotiate a series of cryptographic parameters, including the encryption algorithm, the key exchange algorithm, and the hashing algorithm. The hashing algorithm is used to generate a message digest, or hash, of the data being transmitted. This message digest is then encrypted using a private key and sent to the recipient along with the encrypted data.
The recipient uses their private key to decrypt the message digest and then generates a new message digest of the received data using the same hashing algorithm. If the two message digests match, then the recipient can be assured that the data has not been tampered with in transit and that it originated from the sender, who possessed the private key used to encrypt the message digest.
In SSL/TLS, the choice of the hashing algorithm is critical for ensuring the integrity of the data being transmitted. The most commonly used hashing algorithms in SSL/TLS are SHA-1 and SHA-2 (specifically, SHA-256 and SHA-384).
In addition to being used for message integrity, hashing algorithms are also used in SSL/TLS for certificate validation. When a client connects to a server over SSL/TLS, the server sends its digital certificate to the client. The client then uses the hashing algorithm to generate a message digest of the certificate and compares it to a message digest of the certificate that has been signed by a trusted certificate authority. If the two message digests match, then the client can trust that the certificate was issued by a trusted authority and that the server is who it claims to be.
SHA1 vs SHA256
This article will focus mainly on the differences that exist between SHA1 vs SHA256. SHA2 is the successor of SHA1 and is commonly used by many SSL certificate authorities. There are currently six different SHA2 variants including:
- SHA-224
- SHA-256
- SHA-384
- SHA-512
- SHA-512/224
- SHA-512/256
These variations differ in terms of output size, internal state size, block size, message size, and rounds. To compare the differences that exist between the SHA1 vs SHA256 algorithms, consider the following SHA comparison:
| Algorithm | Output size (bits) | Internal state size (bits) | Block size (bits) | Max message size (bits) | Rounds |
|---|---|---|---|---|---|
| SHA1 | 160 (5 × 32) | 160 | 512 | 264 − 1 | 80 |
| SHA256 | 256 (8 × 32) | 256 | 512 | 264 − 1 | 64 |
Due to SHA1's smaller bit size, it has become more susceptible to attacks which therefore led to its deprecation from SSL certificate issuers in January 2016. An example of the difference in size between SHA1 vs SHA256 can be seen in the following example hashes:
- SHA1 -
da39a3ee5e6b4b0d3255bfef95601890afd80709 - SHA256 -
e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855
With our online hash generator tool, you can quickly generate an SHA256 hash for any string or input value. Simply enter a string value into the input box and select Generate. The tool will then generate a unique 64-digit hash for the value you specified.
Hash collision attacks
A hash collision attack is a type of attack where an attacker generates two different input messages that produce the same hash output. In other words, the attacker is able to find two distinct messages that, when input into the hashing algorithm, result in the same hash value. This type of attack is particularly dangerous for cryptographic hash functions, as it can allow an attacker to forge digital signatures, spoof identities, or create malicious software that can bypass security checks.
SHA1 is an older and weaker hash function than SHA256, and it is vulnerable to collision attacks. In 2005, researchers demonstrated a collision attack against SHA1 that showed it was possible to create two distinct input messages that produced the same hash value. As a result, SHA1 was officially declared insecure by the National Institute of Standards and Technology (NIST) in 2011.
On the other hand, SHA256 is a stronger hash function that is currently considered to be secure against collision attacks. While it is theoretically possible to generate collisions for SHA256, it is currently considered computationally infeasible. This means that finding a collision for SHA256 would require an enormous amount of computing power and resources.
As a result, it is generally recommended to use SHA256 or a more secure hash function for new implementations to ensure the highest level of security.
Brute-force attacks
A brute-force attack is a type of attack where an attacker tries every possible combination of inputs until they find the correct input that generates a given output. In the context of cryptographic hash functions, this means that an attacker is trying to find the input message that produces a specific hash output.
Both SHA1 and SHA256 are vulnerable to brute-force attacks in theory, as there is always a possibility that an attacker could guess the correct input message by trying every possible combination. However, the feasibility of a brute-force attack depends on the size of the hash output and the computational resources available to the attacker.
SHA256 has a much larger output space than SHA1, making it much harder for an attacker to guess the correct input message through a brute-force attack. In other words, SHA256 requires more computational power and time to guess the correct input message than SHA1.
Furthermore, the speed at which an attacker can perform a brute-force attack also depends on the implementation of the hashing algorithm. For example, an implementation that uses hardware acceleration or optimized software could be much faster than a reference implementation.
SHA1 vs SHA256: Which one should you choose?
Our descriptions above suggest what we are getting at.
If you are using SHA1 for digital signatures, message authentication codes, or other applications that require data integrity, you should switch to SHA256. SHA1 is no longer considered secure, and its vulnerabilities make it easier for attackers to perform malicious activities. SHA256 provides better security and is the recommended hash function for these use cases.
If you are using SHA1 for password hashing, you should also switch to SHA256. SHA1 is vulnerable to brute-force attacks, where an attacker tries different passwords until they find the correct one. SHA256 is more resistant to these attacks and provides better security for password hashing.
It is worth noting again that SHA256 is not the only secure hash function available. There are other hash functions, such as SHA3, that provide even better security than SHA256. However, SHA256 is widely used and has been extensively tested, making it a good choice for most use cases.
SHA1 check tool
As SHA1 has been deprecated due to its security vulnerabilities, it is important to ensure you are no longer using an SSL certificate which is signed using SHA1. All major SSL certificate issuers now use SHA256 which is more secure and trustworthy. The following tools can be used to check if your domain is still using SHA1.
- ssllabs - SSLLabs is a great tool that displays a variety of information regarding your domain's SSL certificate. You can use this tool to verify the signature algorithm used, which is located near the top of the report. It should look similar to the following.
Summary
Ensuring that your website is not using an outdated signature algorithm is essential for maintaining the proper security measures for your website. If by chance you run one of the SHA checks above and see that the SHA1 algorithm is being used, you may want to strongly consider purchasing a new SSL certificate that uses SHA256. While there are other secure hash functions available, SHA256 is widely used and has been extensively tested, making it a good choice for most use cases. Remember, security should always be a top priority, and choosing the right hash function is an essential part of keeping your data safe.