The OSI Model – The Layers That Shape Connections
The OSI model is a framework developed in the 1980s to help engineers develop Internet protocols. It's also used today as an educational tool for teaching about networking and communication systems. The purpose of this blog post is to provide insight into how the different layers of the OSI model work together and what they are responsible for. We will discuss each OSI model layer individually to understand how it works with other layers during Internet communications.
The OSI model explained
The Open Sources Interconnection (OSI) model was created by the International Organization for Standardization (ISO) in 1984. The primary purpose of this model was to help engineers develop Internet protocols. An Internet protocol is a set of rules that computers and networking devices use to communicate. This can also be referred to as a "network service". The OSI model provides a structure for understanding how Internet protocols function and allows engineers to create more efficient network services.
Why is the OSI model important?
Even though the OSI model was created almost 40 years ago and the modern Internet does not follow it strictly anymore, it is still useful for troubleshooting network issues. Whether it is a home network with few users or a business network with lots, if you are having connectivity issues, the OSI model can help pinpoint where those problems come from. The seven OSI model layers explain how each type of Internet protocol works together to create a connection between two devices on an IP network.
The layers of the OSI model
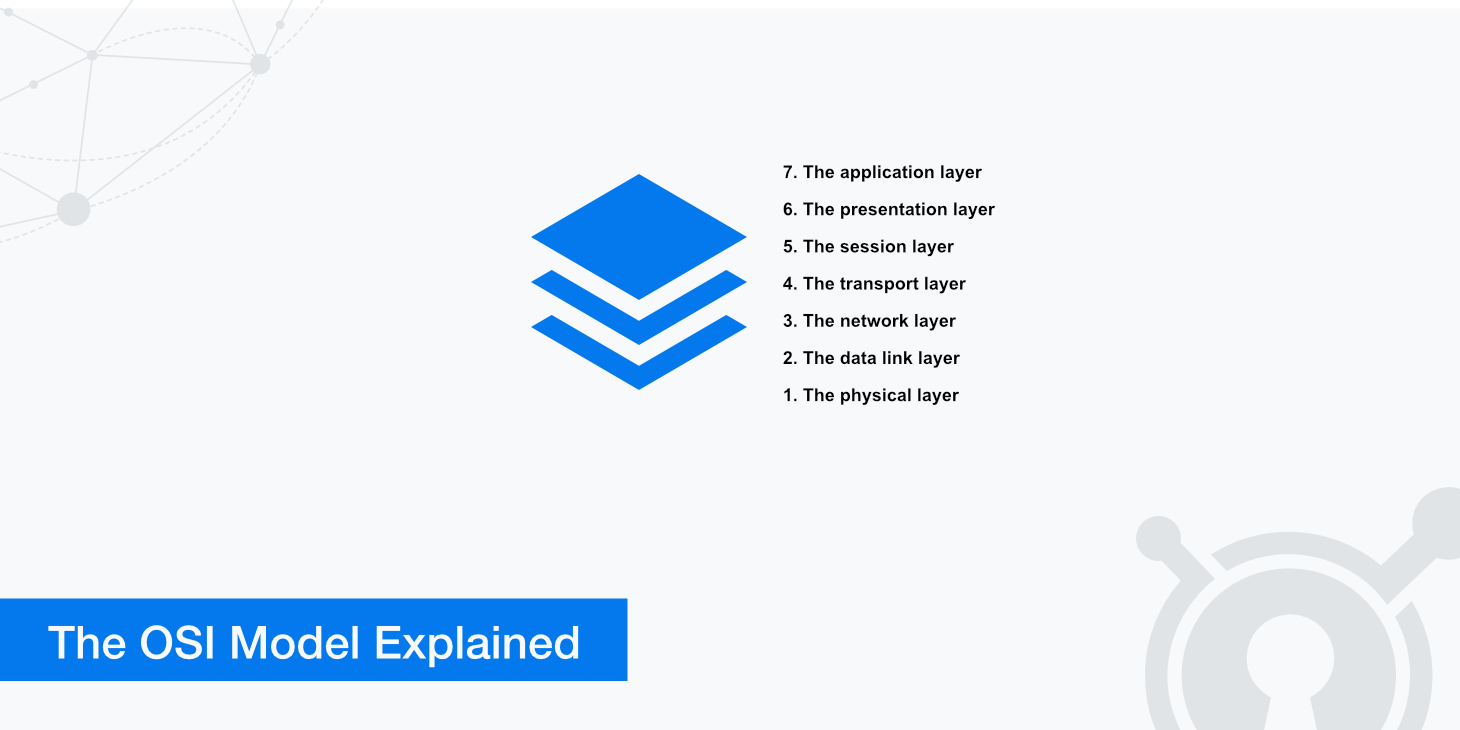
The OSI model defines seven layers, each with its particular function. The purpose of the model is to show how these different functions work together during communication in order to provide end-users with services such as web browsing, emailing, and streaming music or video.
Physical layer
The physical layer is the first and lowest OSI layer, and it's responsible for transmitting bits of data across a network. This can be done via electrical signals, light waves, or radiofrequency transmissions. The physical layer also manages all the hardware components that make up the networking infrastructure. You might see network cables, connectors, and other hardware at this level.
The physical layer is also responsible for building the structure of a network to make it work as intended. This includes things like ensuring that there are no collisions between data packets being transferred over the network or determining how the equipment on different networks can communicate with each other via gateways (routers).
Data link layer
The data link layer is responsible for taking the data that was transmitted by the physical layer and organizing it into packets. It also adds important control information to each packet, such as the destination address and error-checking data. The data link layer is what allows devices on a network to communicate with each other. This layer operates at the hardware level, which means that it uses specific protocols to communicate with network adapters and other devices.
Network layer
The network layer is responsible for routing packets of data between different networks. This can be done either by directing packets to the next closest router or by using a dedicated path known as a virtual private network (VPN). The network layer also manages traffic congestion and oversees all address translation processes. At this layer, you will see protocols such as IPv4 and IPv6.
The data link layer also has two sub-layers of its own: the media access control (MAC) layer and the Logical Link Control (LLC) layer. The MAC layer handles problems with network connections, like ensuring that a device has permission to transmit data over a certain channel. The LLC is responsible for setting up reliable communication between devices on the same physical segment of your local area network (LAN).
Transport layer
The transport layer is responsible for managing connections between network devices and applications. It establishes a communication channel, allowing data to be sent from one device or application to another over the Internet using protocols including TCP and UDP. When data is sent using TCP, it involves a three-way handshake that confirms both sides of the connection are ready to send and receive packets. This layer also manages packet sequencing so that information can be properly delivered in the correct order.
Transport Layer Security (TLS) encrypts communications between applications by allowing sessions to take place over an encrypted channel. This helps to ensure that network traffic remains private, even if it's intercepted by a third party.
Session layer
The session layer creates, manages, and destroys sessions between network devices. A session is simply a temporary connection that's used for exchanging data between two or more devices. This layer uses APIs to allow applications to communicate with each other. It also uses sockets to transport data between applications and the transport layer.
The session layer uses two sub-layers of its own: Simple Network Management Protocol (SNMP) and Remote Authentication Dial-In User Service (RADIUS). Both SNMP and RADIUS use a client/server model, which means that they're able to transmit information securely across network connections. The session layer also manages network connections by determining when it's appropriate to establish sessions and applications. This layer is responsible for accessing the services that are being provided, as well as managing how those individual services interact with each other or protocols from higher layers in order to complete a specific task.
Network File System (NFS) provides filesharing support between multiple devices and applications. It also manages access permissions and controls how files are updated, accessed, or deleted by different devices.
Presentation layer
The presentation layer is responsible for formatting, encrypting, translating, and compressing data so that it can be properly understood by devices on either end of a connection. This includes things like translating text from one character set to another, converting binary information into something that can be read by network devices, and compressing information. At this layer, secure connections are able to be made between web servers and browsers using Secure Sockets Layer (SSL).
Presentation Layer Security uses algorithms that can detect tampering with data such as encryption or compression before it's sent over the network. This helps to ensure that information isn't compromised while it's in transit.
Application layer
As the end-user layer, the application layer is responsible for managing all of the communications between applications on a network. It uses protocols such as FTP, SMTP, and HTTP to send and receive data between devices and networks. The application layer also provides services that allow applications to interact with each other. For example, the File Transfer Protocol allows files to be transferred between devices, while the Simple Mail Transport Protocol allows emails to be sent and received.
Application Layer Security protects communications between applications by encrypting data so that only those with access rights are able to view it. This helps ensure data is protected from unauthorized parties, such as hackers or malware, which may try to intercept information in transit for their own gain.
Data flow through the OSI model
Data flows through the OSI model in a specific order. Each layer uses the information produced by the previous one to process data and create output that can be used by the next layer in line.
For example, data that is being transmitted over a network will first be processed by the physical layer. This layer will determine how the data is to be sent, as well as where it needs to go. The data is then packaged into packets and transmitted across the network. At the receiving end, the packets are unpacked and handed off to the data link layer. This layer will determine if the packets have been received in the correct order and then pass them up to the network layer. The network layer will examine each packet to see where it needs to go and what route it should take.
Finally, the data is delivered to the application layer, which determines what to do with it. Depending on the application, the data may be stored, displayed, or sent to another device.
How security protocols fit into this model
Various types of security protocols are implemented at different OSI layers. For example, network devices may employ firewalls to help protect the network from outside attacks.
Firewall Software: The firewall is a software-based security protocol that helps prevent unauthorized users from gaining access to a device or network and protects against intrusions by hackers, malware, viruses, and other types of malicious code. Firewalls are often used at the data link and network layers of the OSI model.
While firewalls can be installed on your home computer, most businesses and organizations rely on dedicated hardware devices to handle this type of security protocol. This helps ensure that data is properly protected from threats, such as hackers who may try to gain access by disguising their identity or location. As an added layer of security, many businesses and organizations also use intrusion detection systems (IDS), which can detect malicious activity on the network and provide information about the source.
VPNs: A Virtual Private Network (VPN) is a type of security protocol that allows users to connect to a remote network securely. This can be helpful for employees who need to access company files while they are away from the office or for students who need to access their school network from home.
VPNs work by creating a secure tunnel between the user's computer and the remote network. This helps protect data that is being sent over the Internet, as well as preventing others from seeing what websites you are visiting or what files you are accessing.
Data Encryption: Another type of security protocol that can be implemented at different layers is data encryption, which is used to help protect sensitive information from being intercepted by unauthorized parties. Data encryption works by converting plain text into code and back again so only authorized users are able to view it in its original format. This helps ensure that information is only accessible to the parties that need it, such as authorized employees and customers. While encryption can be handled by software on your computer or mobile device, most businesses use dedicated hardware for this purpose.
The bottom line
The OSI model is a helpful way to view the processes that take place when data moves from one device to another. It helps IT professionals understand how information travels and where potential security threats and network errors may occur.
Additionally, you should now realize why it can be beneficial for businesses and organizations to implement multiple types of hardware-based and software-based security protocols. Implementing these protocols at different levels of the OSI model can help ensure that the data is protected from threats in multiple ways.