OCSP Stapling
What is OCSP stapling?
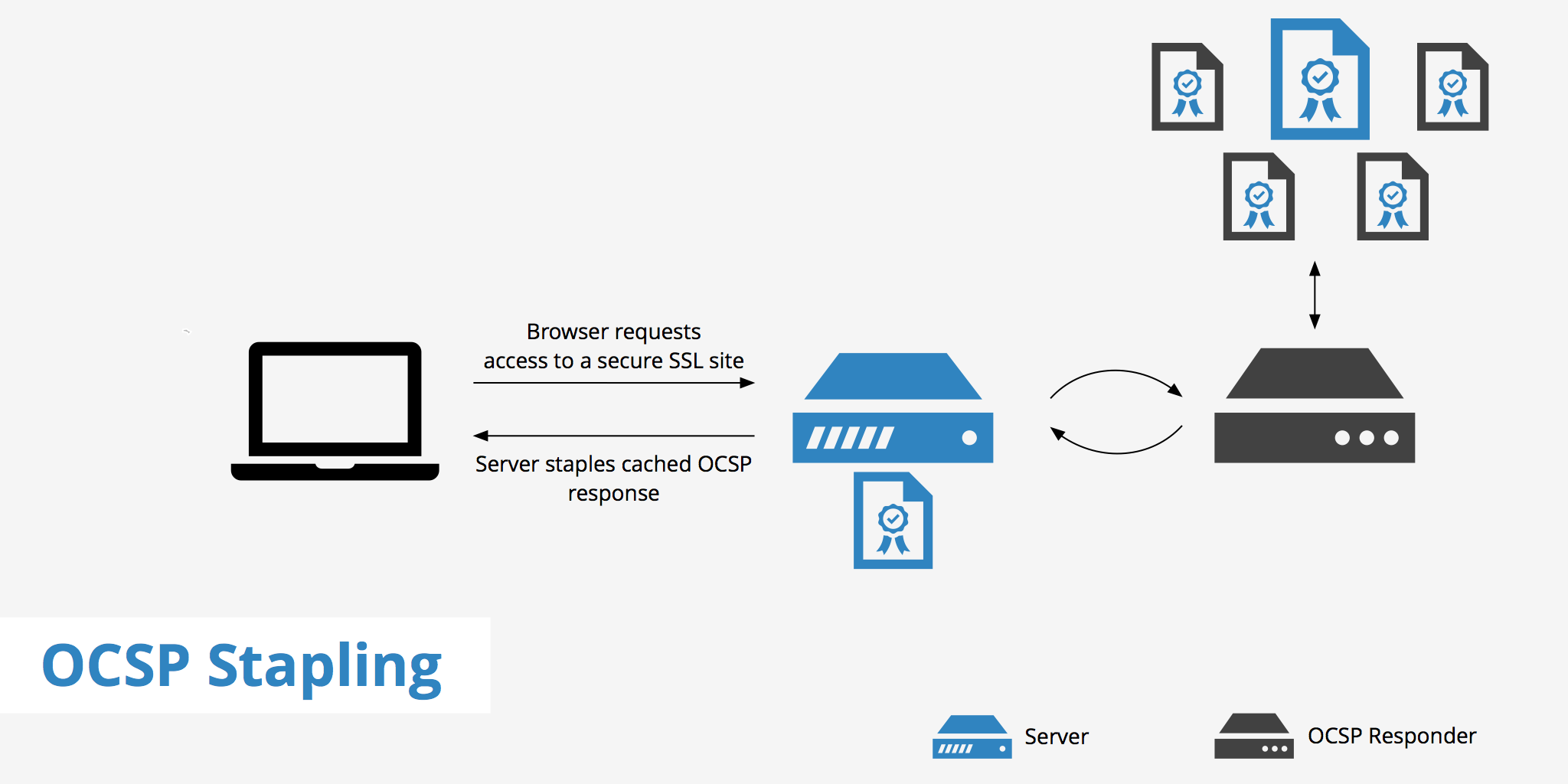
OCSP stapling is an alternative approach to the original Online Certificate Status Protocol (OCSP) for determining whether an SSL certificate is valid or not. It does this by allowing the web server to query the OCSP responder (a certificate authority's server that listens for OCSP requests) and then caches the response. This allows the web server to check the validity of it's certificates and eliminates the need for the client to contact the certificate authority. KeyCDN fully supports OCSP Stapling.
Issues with the original OCSP
The original online certificate status protocol is somewhat inefficient as it requires the certificate authority (CA) to provide responses to each client that requests certificate information. This means that when a certificate is issued to a high traffic website, a large number of requests are sent to the CA's servers asking for certificate validity data.
This is suboptimal as it increases security risks for the user since information must pass through a third party and also slows down loading times.
For example, if a user decides to visit https://www.example.com, since the website is SSL encrypted, the validity of the certificate must be checked. The browser would then query the certificate's vendor (e.g. Namecheap, GoDaddy, etc.) to determine if the certificate is still valid. The user would have to provide the certificate vendor with the URL which it requested which then allows the third party to see who browsed which site at what time.
Furthermore, if the browser isn't able to make contact with the CA for an OCSP response, then the user is brought to a warning screen where they are forced to either continue with the connection anyway or terminate. This can result in false warning messages, thus potentially scaring away users who believe their information may be insecure.
How OCSP stapling works
OCSP stapling is a more efficient way to handle the verification of certificate information.
Instead of making a request to the CA's server for each certificate verification request, OCSP stapling allows the web server to query the OCSP responder directly at regular intervals and cache the response.
When a user attempts to visit the site, the digitally time-stamped response is then "stapled" with the TLS/SSL handshake via the Certificate Status Request extension response. Based on the OCSP response, the browser either displays the web page or shows an error message that the certificate is invalid.
This is both beneficial for performance reasons as well as security. The users no longer have to contact the CA's server individually to receive response of whether or not the certificate is valid. This means the resource burden is now placed back on the certificate vendor and the browser no longer needs to disclose information about users' browsing habits to third parties.
Enabling OCSP stapling on your server
Most modern browsers now support OCSP stapling. For detailed instructions on how to enabled OCSP stapling on your Apache or Nginx server follow these instructions.
Nginx
server {
listen 443 ssl;
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
ssl_certificate /etc/ssl/bundle.crt;
ssl_certificate_key /etc/ssl/your_domain_name.key;
ssl_stapling on;
ssl_stapling_verify on;
}
See this article for a more detailed guide about enabling OCSP stapling in Nginx. Nginx: Enabling OCSP Stapling on Your Server
Apache
SSLStaplingCache shmcb:/tmp/stapling_cache(128000)
<VirtualHost *:443>
SSLEngine on
SSLProtocol all -SSLv3 -SSLv2
SSLCertificateFile /path/to/your_domain_name.crt
SSLCertificateKeyFile /path/to/your_private.key
SSLCertificateChainFile /path/to/DigiCertCA.crt
SSLUseStapling on
</VirtualHost>
See this article for a more detailed guide about enabling OCSP stapling in Apache. Apache: Enabling OCSP Stapling on Your Server
How to verify if OCSP stapling is enabled on your server
If you want to double check that OCSP stapling is enabled on your server you can visit SSL Labs. This site allows you to enter the website URL you want to check and it will in turn provide you a detailed report on certificate details, protocol details, etc. Under the Protocol details section you will see the OCSP stapling field which will indicate whether OCSP stapling is enabled on your server.
Alternatively, you can check for OCSP stapling with the following command:
echo QUIT | openssl s_client -connect example-hexid.kxcdn.com:443 -servername example-hexid.kxcdn.com -tls1 -tlsextdebug -status
Summary
OCSP stapling helps keep users' information secure while also providing a decrease in page load time. By allowing the browser to retrieve SSL certificate information from the server instead of going back to the CA's server for each request, it can achieve both of these results. It is quite uncommon to simultaneously decrease page load times and increase user security, however enabling OCSP stapling makes it easy.