Elliptic Curve Cryptography
In this blog post, we will introduce you to Elliptic Curve Cryptography (ECC), a powerful encryption technique widely used in modern digital communications. ECC is a type of public-key cryptography that is based on the mathematics of elliptic curves, and it is widely considered to be more secure and efficient than traditional encryption methods. In this post, we will explore what ECC is, how it works, and why it is such an important part of modern security.
What is elliptic curve cryptography?
Elliptic curve cryptography, or ECC, is a powerful approach to cryptography and an alternative method from the well known RSA. It is an approach used for public key encryption by utilizing the mathematics behind elliptic curves in order to generate security between key pairs. ECC has been slowly gaining in popularity over the past few years due to it's ability to provide the same level of security as RSA with a much smaller key size.
The resources available to crack encrypted keys continues to expand, meaning the size of encrypted keys must continue to grow in order to remain secure. This can prove to be a burden to certain devices, particularly mobile, that do not have as much available computational power. However, elliptic curve cryptography helps to solve that problem.
How does elliptic curve cryptography work?
An elliptical curve can simply illustrated as a set of points defined by the following equation:
y2 = x3 + ax + b, where a and b are constants.
This graphic looks something like this:
These curves have some interesting properties, such as the fact that any line drawn on the curve will intersect it in three places (including at infinity).
In ECC, we use a specific type of elliptic curve called a "group" that has a defined set of operations. The group is defined by a set of points on the curve, along with a specific point called the "base point." We then define a set of mathematical operations that can be performed on these points, such as addition, subtraction, and multiplication.
To generate a pair of keys in ECC, we start by selecting a random number (called the private key) and using it to perform a multiplication operation on the base point of the curve. The result of this multiplication is the public key, which can be shared with others to encrypt messages.
To encrypt a message using ECC, the sender takes the recipient's public key and performs a series of mathematical operations on it and the message to produce a ciphertext. The recipient can then use their private key (which only they have) to decrypt the ciphertext and recover the original message.
Advantages of elliptic curve cryptography
So why is ECC such an important part of modern security? Here are a few of the key advantages that ECC offers over traditional encryption methods:
Higher security: ECC provides a higher level of security than traditional encryption methods like RSA. This is because the math behind ECC is much more complex and harder to break.
Shorter key lengths: ECC requires shorter key lengths than RSA to achieve the same level of security. This makes it more efficient and faster to use, especially in resource-constrained environments like mobile devices.
Faster processing: ECC is faster to process than traditional encryption methods. This is because the mathematical operations involved in ECC are simpler and require less processing power.
Perfect forward secrecy: ECC provides perfect forward secrecy, which means that even if an attacker is able to obtain the private key at a later time, they will not be able to decrypt messages that were sent using that key in the past.
Resistance to quantum computing: ECC is also more resistant to attacks from quantum computers. Quantum computers are a new type of computer that can perform certain types of mathematical operations much faster than traditional computers. This means that they could potentially break traditional encryption methods like RSA. However, ECC is based on a different type of mathematical problem that is believed to be much harder for quantum computers to solve.
Versatility: ECC can be used in a wide range of applications, from securing online transactions to protecting sensitive data stored on mobile devices. It is also widely used in the Internet of Things (IoT) industry, where it is essential to have a lightweight and efficient encryption method.
Applications of elliptic curve cryptography
ECC is used in a wide range of applications today, from securing online transactions to protecting sensitive data stored on mobile devices. Here are a few of the most common applications of ECC:
SSL/TLS
ECC is widely used in SSL/TLS (Secure Sockets Layer/Transport Layer Security) protocols, which are used to secure online transactions. Many websites now support ECC-based SSL/TLS certificates, which provide a higher level of security than traditional RSA-based certificates.
Digital signatures
ECC is also used for digital signatures, which are used to verify the authenticity of digital documents. Digital signatures are widely used in industries like banking, healthcare, and legal, where it is essential to have a secure and reliable way to verify the authenticity of documents.
Mobile devices
ECC is also widely used in mobile devices, where it is essential to have a lightweight and efficient encryption method. Many mobile devices now support ECC-based encryption, which provides a higher level of security while consuming less battery power and processing resources.
Internet of Things (IoT)
In the IoT industry it is essential to have a lightweight and efficient encryption method. ECC is well-suited for IoT devices, which are often resource-constrained and have limited processing power and battery life.
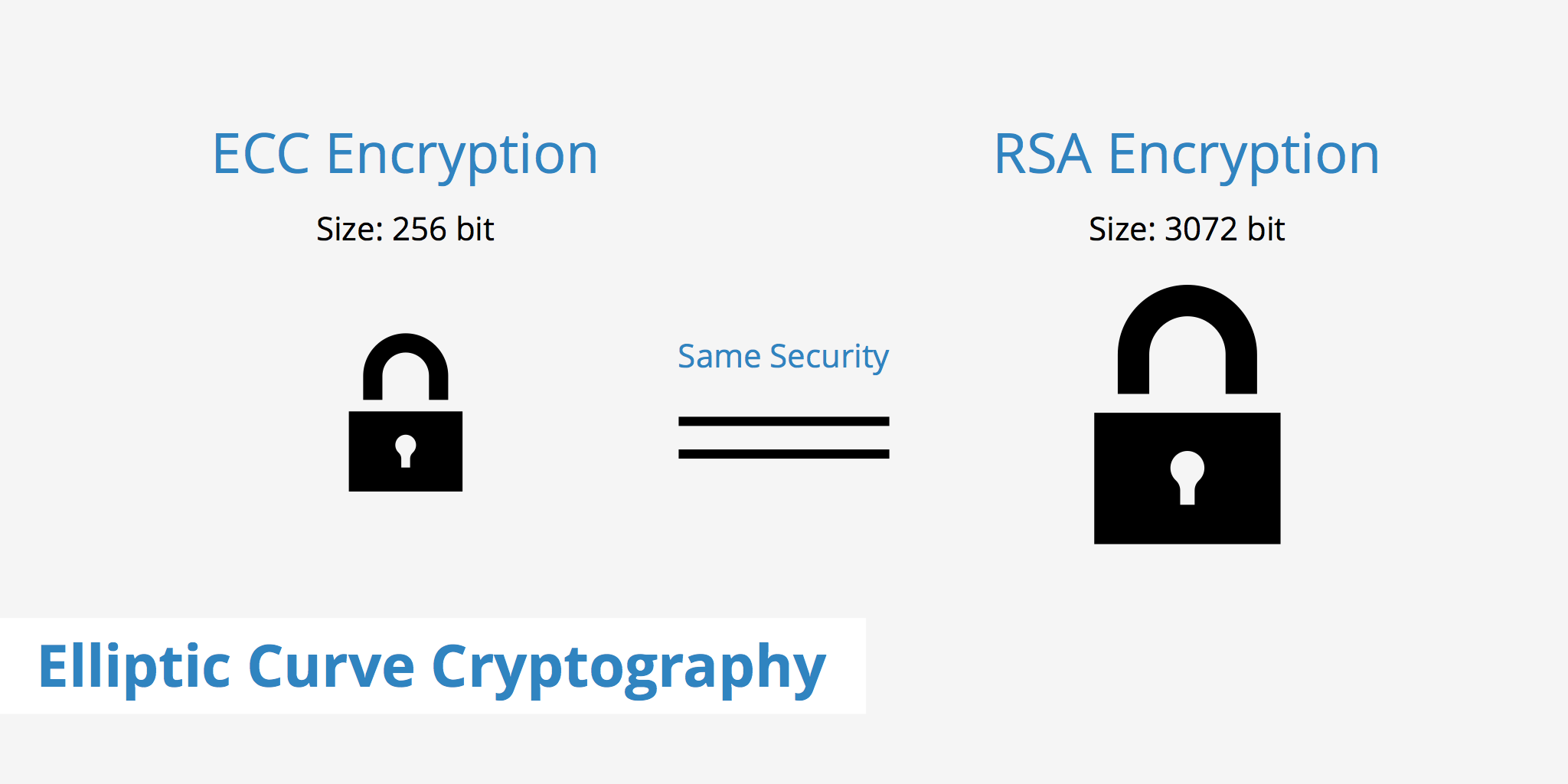
ECC vs RSA
The difference in size to yield the same amount of security between RSA and ECC keys is quite substantial. As can be seen by the comparison table below, for the level of security that can be achieved by an elliptic curve cryptography key of 256 bit requires an RSA key to be 3072 bit. It has been noted by the NSA that the encryption of a top-secret document by elliptic curve cryptography requires a key length of 384 bit. A key length of the same size by RSA would deliver no where near the same level of security.
| RSA Key Length (bit) | ECC Key Length (bit) |
|---|---|
| 1024 | 160 |
| 2048 | 224 |
| 3072 | 256 |
| 7680 | 384 |
| 15360 | 521 |
Why is ECC important?
As noted in the previous section, size is a major factor in the importance of elliptic curve cryptography. For keys of the same size, solving for an elliptic curve discrete logarithm is significantly harder than factoring, which is how RSA encrypts keys.
To put things into perspective, according a Universal Security study, breaking a 228-bit RSA key would take less energy than what is needed to boil a teaspoon of water. Alternatively, breaking a 228-bit ECC key would require more energy than it would take to boil all the water on earth.
Therefore, having the ability to significantly reduce the size of these keys can serve very useful for devices which have less computational power.
Operating system and browser compatibility
According to GlobalSign, elliptical curve cryptography can be used on most of today's modern browsers and operating systems. The list below shows which OS X and browser versions are known to be compatible with ECC.
| Operating System | Minimum Version Required |
|---|---|
| Apple OS X | OS X 10.6 |
| Google Android | 4.0 |
| Microsoft Windows | Windows Vista |
| Red Hat Enterprise Linux | 6.5 |
| Browser | Minimum Version Required |
|---|---|
| Apple Safari | 4 |
| Google Chrome | 1.0 |
| Microsoft Internet Explorer | 7 |
| Mozilla Firefox | 2.0 |
Some organizations are already using this form of cryptography although it currently isn't as widespread and popularized as RSA. Although some companies such as entrust.com are offering ECC demo certificates that allow you to test and devise a rollout plan for once they do become more prevalent.
Summary
In conclusion, Elliptic Curve Cryptography (ECC) is a powerful encryption technique that is widely used in modern digital communications. ECC is based on the mathematics of elliptic curves, and it provides a higher level of security than traditional encryption methods like RSA. Additionally, ECC requires shorter key lengths than RSA to achieve the same level of security, which makes it more efficient and faster to use.
ECC is used in a wide range of applications today, from securing online transactions to protecting sensitive data stored on mobile devices. It is also widely used in the IoT industry, where it is essential to have a lightweight and efficient encryption method.
As more and more data is transmitted over the internet, it is essential to have strong encryption methods like ECC to ensure that our data remains secure and private. With its higher level of security, shorter key lengths, and resistance to quantum computing, ECC is a vital part of modern security, and it will continue to play a critical role in securing our digital communications in the future.