DDoS Attack
In today's world, the internet has become a vital part of our lives, and we rely on it for almost everything. It has brought us convenience and connected us to the world like never before. However, as much as it has helped us, it has also exposed us to various threats. One of the most significant threats that we face is DDoS attacks. In this article, I will explain what a DDoS attack is, how it works, and what measures you can take to protect yourself and your business from such attacks.
What is a DDoS attack?
DDoS stands for Distributed Denial of Service. It is a type of cyber attack in which an attacker tries to make a website or an online service unavailable by overwhelming it with traffic from multiple sources. The goal of the attacker is to consume all the resources of the target website, making it impossible for legitimate users to access it. In simple terms, a DDoS attack is like a traffic jam on the internet, which makes it impossible for anyone to get through. Unlike other attacks, DDoS attacks are not meant to steal information or impose security risks but rather are meant to make the website inaccessible which can cause great loss to any online business.
How does a DDoS attack work?
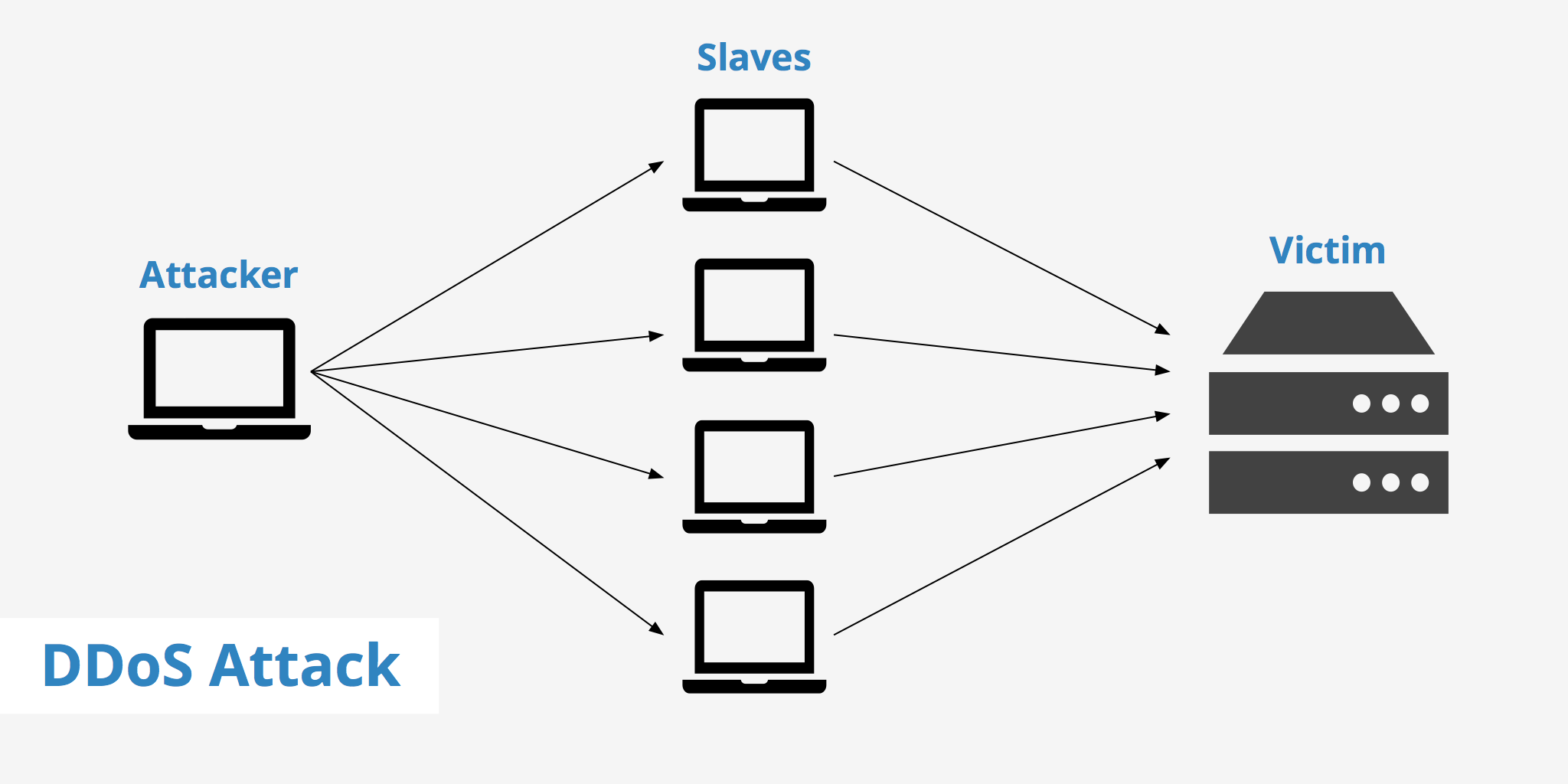
A DDoS attack works by flooding the target website or online service with a massive amount of traffic. The traffic is generated from multiple sources, which makes it difficult to block the attack. The attacker usually controls a network of infected computers called a botnet. The botnet is made up of computers that have been infected with malware, allowing the attacker to control them remotely.
Once the botnet has been set up, the attacker sends commands to it, directing it to send traffic to the target website or online service. The traffic generated by the botnet is usually more than the target website, or online service can handle, causing it to become unresponsive or crash. In some cases, the attacker may use multiple types of DDoS attacks simultaneously to increase the chances of success.
DoS vs DDoS
DoS (Denial of Service) and DDoS (Distributed Denial of Service) are both types of cyber attacks that aim to make a website or an online service unavailable to legitimate users. However, the main difference between the two is the number of sources used to carry out the attack.
A DoS attack usually targets a victim at the application layer. A DoS attack is accomplished by a single user using a single internet connection.
A DDoS attack on the other hand, takes advantage of using multiple infected devices across different IP addresses to deliver a similar attack, however at a much larger scale. DDoS attacks are harder to deflect than DoS assaults simple due to the large volume of devices contributing to the attack. DDoS attacks can be accomplished at the application layer however are also used at the network layer to target network infrastructure.
Types of DDoS attacks
There are several types of DDoS attacks, and each one works differently. Below are some of the most common types of DDoS attacks:
Network layer
Network layer attacks (also known as layer 3 or 4 attacks) are attacks designed to specifically target the victim's network infrastructure. These attacks are most commonly carried out via DDoS and can cause severe damage as well as cost significant amounts of money for the victim. Examples of attacks within this category include DNS amplification, SYN Flood, and NTP DDoS attacks. Each of these attacks takes advantage of different vulnerabilities that exist within certain protocols, parts of the server, etc.
DNS amplification for instance involves the use of open DNS resolvers to send a large amount of traffic to the victim's infrastructure. The attacker sends a small request to an open DNS resolver, which then sends a much larger response to the victim's IP address, resulting in an amplification of the traffic.
SYN Flood makes use of the TCP protocol to perform a DDoS attack. TCP connections are established by the client sending a SYN packet to the server and then the server responding with an ACK (acknowledged). SYN Flood takes advantage of this by sending a large amount of SYN packets and ignoring the ACKs returned by the server. This method exploits the limited amount of TCP connections that are allowed to be open on a server thus preventing legitimate users from accessing the website.
NTP attacks take advantage of the Network Time Protocol to overwhelm the victim with User Datagram Protocol (UDP) traffic. The attacker in this case would sends multiple requests for "get monlist" which returns a list of the last 600 hosts who have connected to that server. The attacker would then spoof the requesting IP to that of the victim, resulting in the amplification of traffic to that server and eventually limiting its use.
All of these Network Layer DDoS attacks involve overwhelming the victim's network resources with a large amount of traffic. These attacks are often difficult to defend against, as they involve exploiting vulnerabilities in widely-used protocols, such as DNS and NTP, or exploiting the fundamental mechanisms of network communication, such as the three-way handshake of TCP.
Application layer
In contrast to Network Layer DDoS attacks, which target the infrastructure layer of the victim's network, Application Layer attacks (also referred to as a layer 7 attack) target the web application layer of the victim's server. These attacks aim to consume server resources by sending malicious requests that appear to be legitimate traffic.
An application layer attack can be either carried out via DoS or DDoS. The application layer is responsible for the for the functionality of HTTP, FTP, SMTP, etc. which is exactly what this category of attack targets. The attack seeks to overload the system's resources by depleting it's RAM / CPU for example. It does this by sending a large number of requests to the system.
Application Layer DDoS attacks can take several forms, including HTTP flood, Slowloris attacks, and Application layer protocol attacks.
HTTP floods: HTTP Floods involve sending a large number of HTTP requests to the victim's server, with the goal of overwhelming the server's resources and making the website unavailable to legitimate users.
Slowloris attacks: Slowloris attacks involve sending partial HTTP requests to the victim's server and keeping the connection open for as long as possible, consuming server resources and preventing legitimate users from accessing the website.
Application layer protocol attacks: These types of attacks exploit vulnerabilities in specific application layer protocols, such as FTP (File Transfer Protocol) or SIP (Session Initiation Protocol), to consume server resources and make the web application unavailable to legitimate users.
The main difference between Network Layer and Application Layer DDoS attacks is the layer of the OSI model that is targeted. Network Layer attacks target the infrastructure layer, while Application Layer attacks target the application layer. Application Layer DDoS attacks are often more difficult to defend against, as they exploit vulnerabilities in web applications that are often difficult to identify and mitigate.
Volumetric attacks
Volumetric attacks (or flood attacks) are characterized by a high volume of traffic being sent to the victim's server or network, often using a botnet or other network of compromised devices to generate a massive amount of traffic. The traffic generated by the attacker is usually in the form of UDP, ICMP, or TCP packets. These attacks can be either Network Layer or Application Layer attacks, depending on the type of traffic being sent.
Protocol attacks
Protocol attacks exploit vulnerabilities in network protocols, such as TCP or UDP, to consume server resources and make the server unavailable to legitimate users. These attacks are typically Network Layer attacks.
Reflective attacks
Reflective attacks involve using a third-party server to send a large amount of traffic to the victim's server, making it appear as if the traffic is coming from legitimate sources. These attacks can be either Network Layer or Application Layer attacks.
IoT botnet attacks
IoT Botnet attacks involve the use of a network of compromised IoT (Internet of Things) devices to generate a large amount of traffic and overwhelm the victim's server or network. These attacks can be either Network Layer or Application Layer attacks, depending on the type of traffic being generated.
How to protect yourself from DDoS attacks
There are a few ways to help protect yourself against DDoS attacks.
Use a DDoS mitigation service:
A DDoS mitigation service can help protect your website or online service from DDoS attacks. The service works by detecting and blocking malicious traffic before it reaches your website or online service.
Use a Content Delivery Network (CDN)
A CDN can help protect your website or online service from DDoS attacks by distributing the traffic across multiple servers. This helps to reduce the load on any one server, making it more difficult for an attacker to overwhelm your website or online service.
Use firewalls
A firewall can help protect your website or online service from DDoS attacks by blocking malicious traffic. Firewalls can be configured to detect and block traffic from known malicious sources, reducing the chances of a successful DDoS attack.
Monitor network traffic
It is essential to monitor network traffic regularly to detect any unusual patterns that may indicate a DDoS attack. Monitoring tools can help you identify the source of the traffic and take measures to block it.
Keep software up-to-date
Keeping your software up-to-date is crucial in protecting your website or online service from DDoS attacks. Updates often include security patches that address known vulnerabilities, reducing the chances of an attacker exploiting them.
Use strong authentication
Using strong authentication measures, such as multi-factor authentication, can help prevent unauthorized access to your website or online service. This can prevent attackers from gaining access to your resources and using them to launch a DDoS attack.
Educate employees
Educating employees on cybersecurity best practices can help reduce the risk of a DDoS attack. Employees should be aware of the dangers of phishing attacks and the importance of keeping passwords secure.
KeyCDN closely mitigates DDoS attacks in the background to help keep our users' websites safe. Our edge servers are being continuously monitored to detect and rectify any possible attacks.
Summary
DDoS attacks can have devastating consequences for individuals and businesses. They can cause websites and online services to become unavailable, resulting in lost revenue and reputational damage. It is essential to take measures to protect yourself and your business from DDoS attacks. Using a DDoS mitigation service, CDN, firewalls, and strong authentication measures can help reduce the risk of a successful attack. Regular monitoring of network traffic and keeping software up-to-date can also help prevent DDoS attacks. Educating employees on cybersecurity best practices is crucial in reducing the risk of a successful DDoS attack. By taking these measures, you can help protect yourself and your business from the threat of DDoS attacks.