What Is a Certificate Revocation List (CRL)?
A certificate revocation list, or CRL for short, is a list of certificates that have been revoked before their expiration date by certificate authorities. There can be many reasons as to why a certificate was revoked (we'll explain this further in the next section). However, the main idea here is to provide a central location for web clients such as browsers to check whether or not a site's SSL/TLS certificate is trustworthy.
This post will cover what can cause a certificate to be revoked, how CRL's work, and a few CRL tools you can use to check whether a certificate is revoked or not.
Why do certificates get revoked?
There are various reasons why a certificate might get revoked. Before getting into the specifics, it should be noted that a revoked certificate does not mean an expired certificate but rather an active certificate that has been "retired" so to speak. According to RFC 5280, the reasons for which a certificate can be revoked include:
- unspecified
- keyCompromise
- cACompromise
- affiliationChanged
- superseded
- cessationOfOperation
- certificateHold
- removeFromCRL
- privilegeWithdrawn
- aACompromise
The reasons defined above however, may not be completely clear. Therefore, here are three common real-world examples of reasons why a certificate may be added to a revocation list.
- The private key has been lost or compromised, therefore it can no longer be trusted
- The previous owner of a domain no longer owns that domain or ceases operations entirely
- The certificate was discovered to be counterfeit
How does a certificate revocation list (CRL) work?
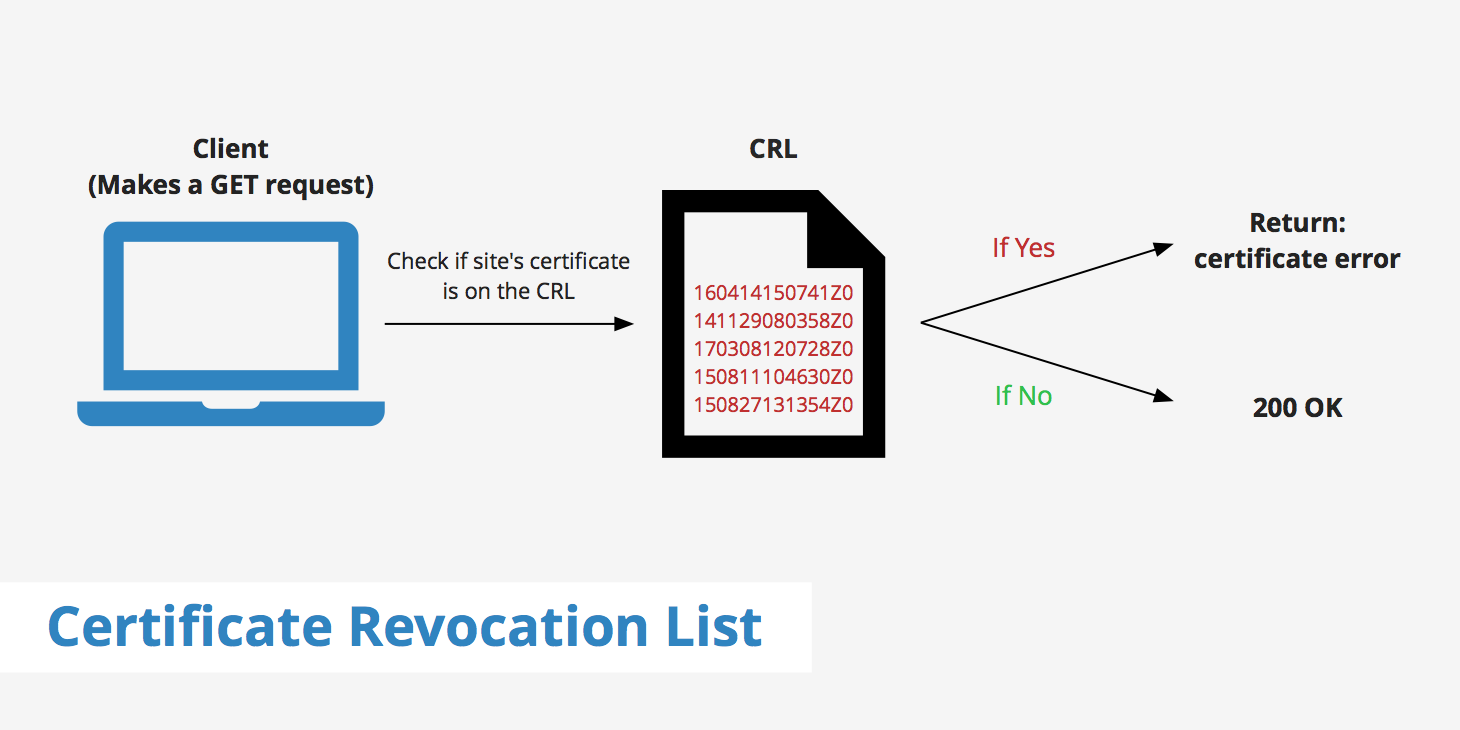
The certificate revocation list is essentially a large list of blacklisted certificates maintained by certain certificate authorities. When a browser makes a request to a page that has an SSL/TLS certificate, it follows the process below.
- A
GETrequest is made to an HTTPS-enabled page. - The certificate authority receives that request and returns a list of all revoked certificates.
- The browser then parses the CRL to ensure that the certificate of the requested site isn't contained within it.
Maintaining a certificate revocation list can be difficult. It requires continuous updates and changes and therefore is susceptible to errors. Furthermore, depending on when the CRL was last updated, it's possible that a browser request to a site that should have a revoked certificate gets a green light since the list wasn't updated in time.
Certificate revocation list tools
There are a couple of ways you can check a certificate authority's CRL. One of which is through using Google Chrome and checking the certificate details. To do this, open the Chrome DevTools, navigate to the security tab and click on View certificate.
From here, click on Details, and scroll down to where you'll see "CRL Distribution Points".
The link associated with this Extension will provide you with the list of serial numbers for certificates of that authority that have been revoked.
Additionally, certain certificate authorities provide on-site lists of their revoked certificates:
CRL vs OCSP
As previously mentioned, updating and constantly maintaining a certificate revocation list can become quite cumbersome. Many certificate authorities don't even keep their CRL up to date anymore. Furthermore, retrieving a CRL can slow things down a fair bit depending upon how large the CRL file is.
That's why many browsers and certificate authorities now favor OCSP stapling as opposed to CRLs to determine whether a certificate is valid or not. OCSP stapling works by allowing a web server to query the OCSP responder do determine whether a certificate is valid or not. The web server is then able to cache the response eliminating the need for the client (i.e. web browser) to query the certificate authority.
OCSP stapling's primary benefits over using CRLs are that it requires less bandwidth and it enables real-time status checks.
Summary
Although certificate revocation lists aren't used as much as they were in the past, it is still good to know what they are how they differ from the current solution. If by chance you do need to verify if a particular certificate has been revoked, use the methods mentioned in this guide to find a list of revoked certificates that have been deemed untrustworthy by your certificate authority.